
Ensure your technology is secure, efficient, and future-ready. Use our Business Tech Health Checklist to uncover risks, optimize performance, and stay ahead—because healthy systems drive healthy business growth.
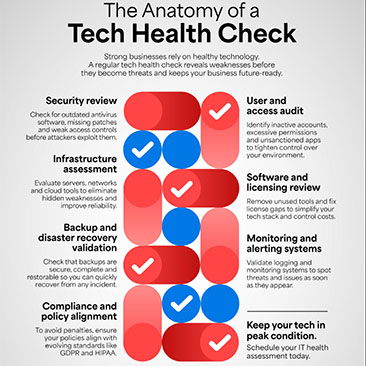
Strong businesses rely upon healthy technology. A regular tech health check reveals weaknesses before they become threats and keeps your business future-ready. Our Anatomy of a Tech Check inforgraphic will get you started.
Forward thinking leaders invest in technology that drives speed, scalability, and better customer experiences. This starts with a technology budgeting process that works for you instead of quietly working against you.

A strong tech budget is your roadmap for growth, where every technology investment drives progress. This checklist shares the five steps to help you make smarter budgeting choices that deliver real results.

Sixty-six million years ago, dinosaurs didn’t adapt, and they didn’t survive. Cyberthreats are threatening businesses with security practices stuck in the past. Discover what’s extinct, what’s evolved and what you need to do to survive.

Avoid digital extinction by adopting zero trust, AI-driven defense, cyber-aware culture, resilience, and supply chain security—empowering leaders to adapt and resist attacks. Cyberthreats are the meteors of our new digital age.